Security & IT 101: The Basics
The Top 5 Cybersecurity Essentials

1. Take Your SATs: Security Awareness Training
Human error is the root cause of many breaches. Training employees to recognize phishing, scams, and unsafe behaviors dramatically reduces risks. This is foundational for any organization, regardless of size or industry. Security Awareness Training is a rudimentary first step and required in any compliance regulation or cyber insurance policy.
This one is a no-brainer, can be implemented in a matter of days, and costs anywhere between $1 to $5 per user per month.
Any SAT solution worth its salt will also have phishing simulation built-in. This helps organizations test employees' ability to recognize phishing attempts and identify areas needing targeted training. It also promotes a culture of vigilance, making staff more cautious with suspicious emails.
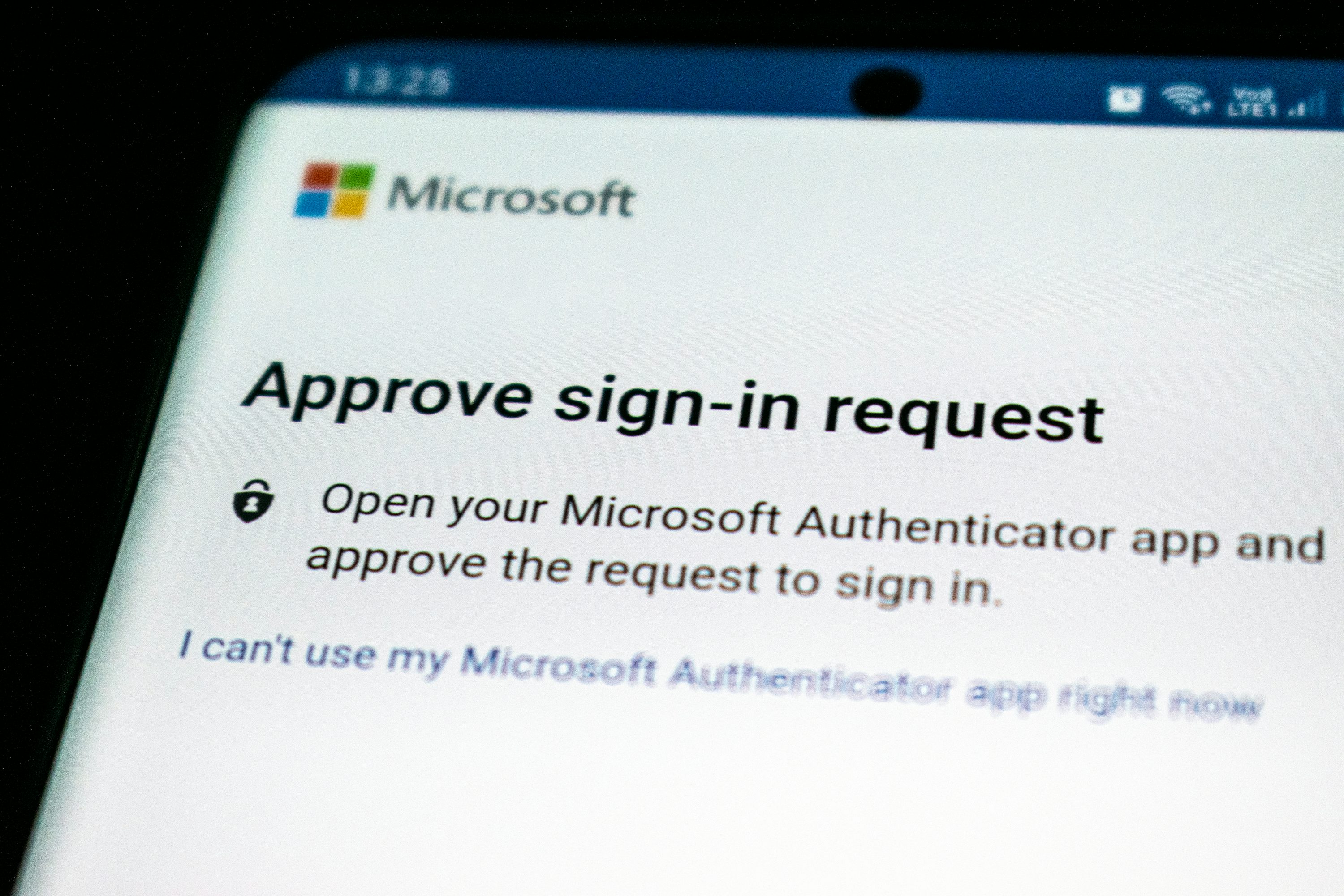
2. MFA: Multifactor Authentication
Passwords alone are no longer enough. Enable Multifactor Authentication (MFA) wherever possible. MFA adds a critical layer of defense, protecting accounts even if passwords are compromised. MFA enhances security by requiring additional verification steps from different categories:
Something you know: Information only you should know, like a password or PIN.
Something you have: A physical device you possess, such as a phone or security key that receives a verification code.
Something you are: A unique biological characteristic, like your fingerprint or facial recognition.
All three factors provide the highest security, but using any two of the three is considered the minimum standard, often referred to as Two-Factor Authentication (2FA).
While basic MFA options like SMS or email OTPs are common, security experts recommend using authenticator apps (e.g., Google Authenticator, Microsoft Authenticator) or hardware tokens, as they are more secure against threats like SIM swapping or email compromise.
Many apps you already use have MFA settings built-in—simply go into the account settings to activate it. In most cases, enabling MFA comes at no additional cost.
For online applications that don't support MFA, implement a Password Manager to enforce unique, complex passwords across all accounts, or consider centralized passwordless solutions (see #5 below).

3. EDR: Endpoint Detection and Response
4. Patch & Backup: Stay Updated and Prepared
Patching and backups have been an essential practice since the first computers were available. They close security gaps and protect data. Regular patching prevents attackers from exploiting system vulnerabilities. Automated tools can streamline this process, with updates ideally applied as soon as they're available or scheduled during off-hours.
Backups act as a safety net against data loss from accidental deletions, ransomware, or system failures. With so many systems in the cloud today, too many think backups aren't necessary. However, just because your systems are in the cloud doesn't mean it's backed up—cloud services often focus on availability, not long-term data recovery—a backup is almost never included.
Follow the 3-2-1 rule: keep three copies of your data, on two different media, with one stored offsite (or in the cloud). Cloud-based backups for Microsoft 365 and Google Workspace can cost as little as $2 per account per month.
For enhanced business continuity, consider Disaster Recovery as a Service (DRaaS). DRaaS enables rapid recovery of systems and data during major incidents, minimizing downtime and ensuring ensuring you're back up and operational in minutes, not days.

5. Password Managers (PM) & Policies
Why these 5?
These measures represent the most basic and fundamental security & IT steps that address common vulnerabilities businesses face. They are straightforward to implement, cost-effective, and provide a significant boost to your security posture. Together, they form a strong foundation for a robust cybersecurity strategy.
If your company already has these five essentials in place—plus additional security measures—kudos to you! You understand that cybersecurity is an ongoing process, like a never-ending game of chess (or better yet, GO!). Strategies and tactics evolve constantly, making vigilance key to success. Contact us now to get a 3rd-party, objective, evaluation of your current security measures and validate what you have in place and identify and gaps needing coverage.
If your company has only implemented these five, you're ahead of many and off to a solid start. Let's connect to schedule your C9 Security Evaluation and create a customized roadmap for continued security growth.
If you're unsure, only have a few, or if you know your company has none of these essentials in place, don’t wait. Contact Cloud 9 today for expert guidance and support.

These measures represent the most basic and fundamental security & IT steps that address common vulnerabilities businesses face. They are straightforward to implement, cost-effective, and provide a significant boost to your security posture. Together, they form a strong foundation for a robust cybersecurity strategy.
If your company already has these five essentials in place—plus additional security measures—kudos to you! You understand that cybersecurity is an ongoing process, like a never-ending game of chess (or better yet, GO!). Strategies and tactics evolve constantly, making vigilance key to success. Contact us now to get a 3rd-party, objective, evaluation of your current security measures and validate what you have in place and identify and gaps needing coverage.
If your company has only implemented these five, you're ahead of many and off to a solid start. Let's connect to schedule your C9 Security Evaluation and create a customized roadmap for continued security growth.
If you're unsure, only have a few, or if you know your company has none of these essentials in place, don’t wait. Contact Cloud 9 today for expert guidance and support.

These measures represent the most basic and fundamental security & IT steps that address common vulnerabilities businesses face. They are straightforward to implement, cost-effective, and provide a significant boost to your security posture. Together, they form a strong foundation for a robust cybersecurity strategy.
If your company already has these five essentials in place—plus additional security measures—kudos to you! You understand that cybersecurity is an ongoing process, like a never-ending game of chess (or better yet, GO!). Strategies and tactics evolve constantly, making vigilance key to success. Contact us now to get a 3rd-party, objective, evaluation of your current security measures and validate what you have in place and identify and gaps needing coverage.
If your company has only implemented these five, you're ahead of many and off to a solid start. Let's connect to schedule your C9 Security Evaluation and create a customized roadmap for continued security growth.
If you're unsure, only have a few, or if you know your company has none of these essentials in place, don’t wait. Contact Cloud 9 today for expert guidance and support.


